Surely everyone has encountered spam at least once in their life. It rains down on us with enviable regularity not only from the World Wide Web, but also in real life. The same countless advertising booklets in the mailboxes at the entrance annoy almost everyone. In the age of computer technology, the quality and characteristics of spam have changed markedly. It is no longer necessary to hire offline couriers, but it is enough just to find out your email address. In addition to harmless advertising of local stores with beautiful images of products and written reviews for them, spam can be a real threat to your wallet. So you need to be extremely careful with such letters. But first things first.
From our article you will learn what the essence of spam is, what types of mailings there are and how to deal with it.
Types of spam
The essence of spam is to convey the advertised product to the end user. And it doesn't have to be a product from a store. Some increase traffic to their sites, others work on referral systems, others spread viral code, others warn us about the next end of the world, etc. Motives, varieties, andat the same time, there can be many, many examples of spam.
This is the most common form of spam today. Everyone who is connected to the World Wide Web has e-mail. Without it, it is impossible to register on social networks and on other sites. Mail helps you communicate with friends, conduct business correspondence, share files, etc.
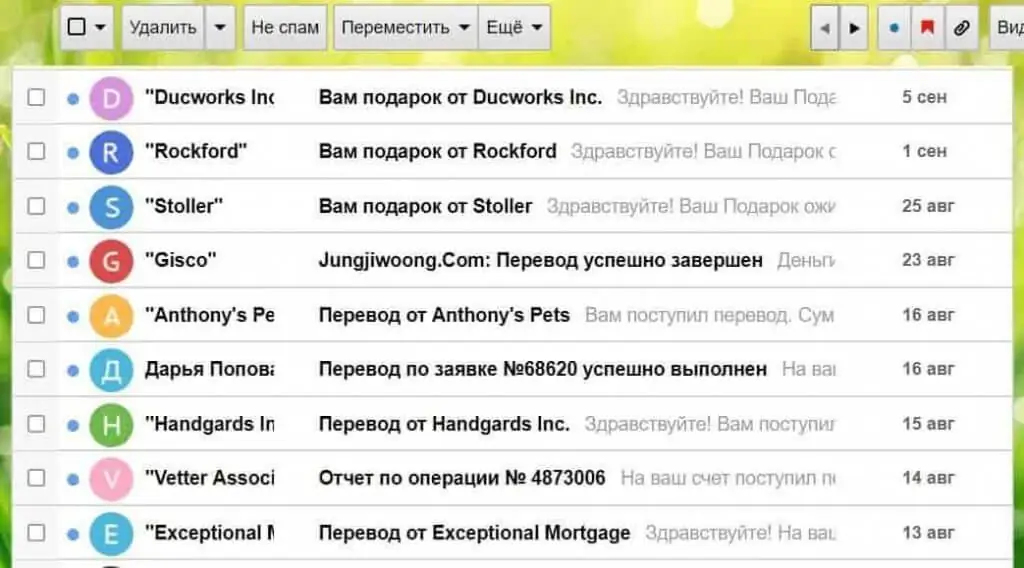
Most users check their email every day, and some more often. Accordingly, letters that get to the mail are likely to be read at least within a day. Spammers are well aware of this and use the appropriate tools for their mailings.
One of the most common examples of a spam message is a tempting offer to get rich quick. The attachment may contain charts, screenshots of payments, videos and reviews of individuals who have already tried this service. Naturally, all this information is fake, although it sometimes looks quite convincing.
Many large mail services, such as Gmail, Yahoo or Yandex, taking into account numerous examples of spam advertising, create their own filters and actively fight junk in users' email boxes. Nevertheless, this still does not stop spammers, and they continue their dishonorable work.
Social networks
You can see many striking examples of spam text on social networks. Services "VKontakte", "Odnoklassniki", "Instagram", "Facebook" and others are already completely spammed with messages, fake groups and otherharmful advertising elements.
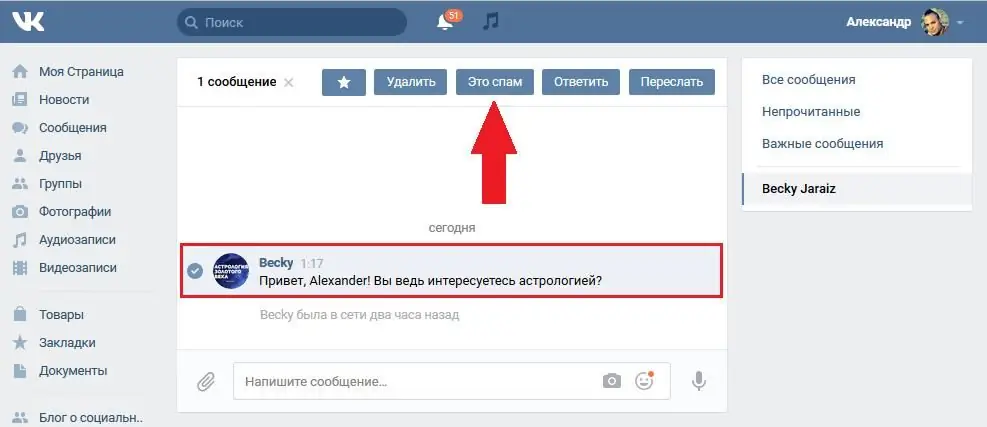
At first, dealers distributed the texts they needed through private messages directly from their accounts. But ordinary users, together with moderators, began to actively fight against this phenomenon. It didn't take long for the spammers to start using a different, tougher technology.
They started hacking ordinary accounts using phishing sites (fake resources duplicating some social network) and from them they sent their messages to the owner's friends and subscribers. In this case, you can disable spam only by removing the "hacked" friend from your contacts.
Forums
Forums are a number of specific resources configured for communication of some users with others. Some sites allow you to exchange not only text information, but also transfer some files: images, video, audio, and more.
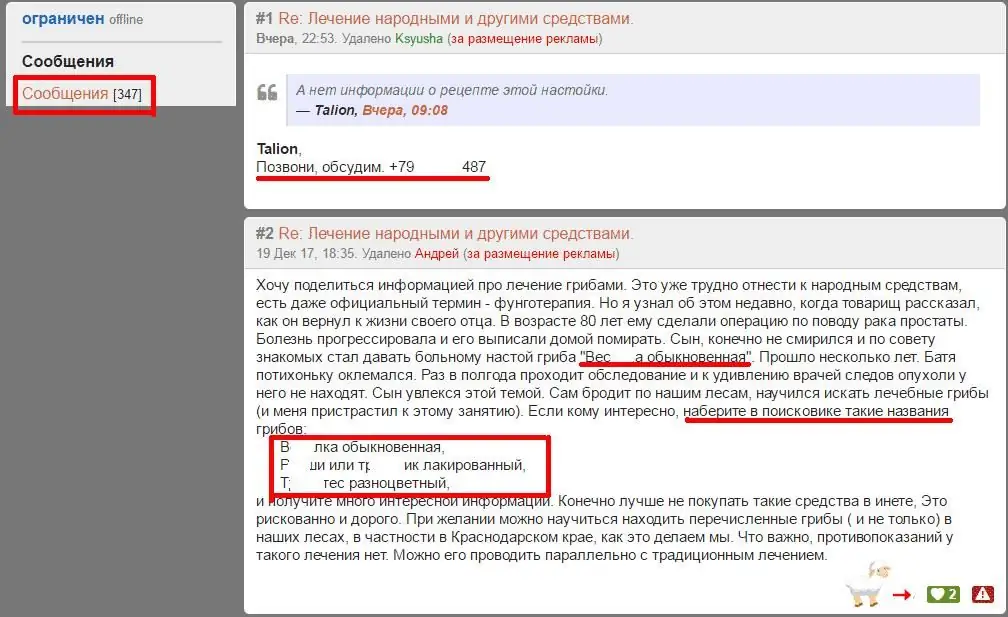
There are a lot of opportunities for PR of your products or services. There are also plenty of examples of spam. The user can leave the necessary links or other mentions both in his profile, which is displayed on the site, and in the discussion threads. Spammers create a seemingly normal topic on a decent forum, but only to stuff it with their links.
Administrators of such resources are trying to deal with such harmful elements in different ways: they include pre-moderation of comments, enclose texts in nofollow tags, ban and delete suspicious accounts, etc. Someadmins write or order special scripts, where various examples of spam are collected, and if it appears, they delete the message or immediately - the user who left it.
Comments on websites
Here we are talking about various thematic resources and blogs. Fraudsters also actively use such sites for their unclean deeds. Among other examples of spam, one can distinguish a separate and largest category of dealers in this segment, who advertise their own websites and blogs by leaving comments with links under the posts.
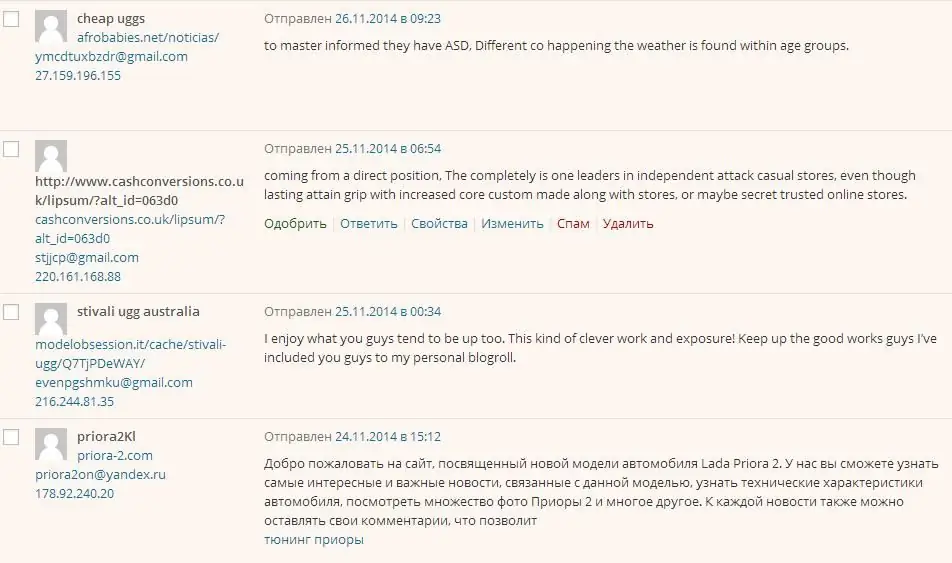
This is necessary to raise the IQS indicator (site quality index, former TIC). The latter contributes to good search results, as well as monetization of the resource. It is easier to deal with such spam than in other cases. Pre-moderation of comments acts as a panacea here. It also helps to ban users by IP address and use advanced captchas.
Catalogs and bulletin boards
About the same situation as with the comments on the site, occurs on the bulletin boards. A striking example is the large Avito resource, where literally in every section you can find spam in various forms.
It can be both in the ads themselves and in ad units on the side or bottom. Avito is wildly popular in Russia, and you can pay for a banner that supposedly contains regular advertising, but in reality it is spam. In addition, moderators cannot cope with thousands of ads and cannot guarantee with 100% probability the absence of links and somereferences to third-party resources.
SMS
Mobile gadgets are also a haven for scammers. Spam viruses are very common here, and of an extremely harmless nature. Some SMS can easily reset the balance of your phone or, worse, your bank card.

Scammers go to different tricks to achieve their goals. Out of a thousand SMS sent to a variety of numbers, at least one will “shoot”. As a rule, spammers ask to send a response message disguised as a harmless procedure. For example, confirm that you are not a robot by sending SMS to a short number. Large and reputable services and companies can be indicated as a sender: Sberbank, Gosulugi, RIA-Novosti, the same Avito and others.
How spammers build their bases
Scammers collect email addresses and phone numbers from all available sources. Among others, thematic forums, guest books, social networks and other resources are especially popular, where such information is poorly protected or is even in the owner's profile in the public domain. Some databases are hacked by hackers and sold on the Darknet.

In addition, the collection of personal information may be carried out programmatically. There are special search bots - harvesters. They go through thousands of resources in an hour and carefully put all the data they receive into the database.
It is also worth taking into account the usual selection. Billions of mailboxes are registered around the world, which means that withusing a specially written program, you can generate these addresses. The same is true for phones. It is no secret that for each Russian region, operators have allocated their own codes indicating the ownership of the number. For example, +7 (918) xxx-xxx-xx is the Krasnodar Territory with the Rostov Region. The scammers only have to generate the remaining seven digits and spam evil, already taking into account the specifics of a particular region.
Help dishonest businessmen and viruses. Malicious code, usually worms, can send itself to the address base. The information collected in this way is extremely valuable for spammers, because it contains only work data used by their owner.
How to get rid of spam?
Here we will consider the situation with e-mail, because mailbox spamming is the main headache for most netizens. After your e-mail got into the database of scammers, they will not leave you just like that.
However, it is possible to significantly reduce the likelihood of being included in such a list if you take simple precautions. Experienced users strongly recommend starting, in addition to the main mailbox, an additional one, and preferably several. The latter can and should be used to register on forums and other sites where an email address is required.
The next thing is suspicious emails. If you are asked to follow an unfamiliar link in order to receive a reward, complete registration, buy a yacht for a couple of thousand, or something else, although you have not previously visitedthis site, it is better to immediately delete the letter. It should also be noted that some scammers put a viral code on the "Unsubscribe" button.
New mailbox
If you are going to start a new mailbox, then you should not choose a simple and easy-to-remember name for it. Make it as complex, confusing and long as possible. Smudge boxes are great for companies and other services, but they're useless for the average user.
You will still send it to your friends electronically by copying the address. But it will be much harder for spam bots to generate such a complex name.
Mail services
Judging by the numerous reviews from users from all over the world, the most interesting service in terms of spam filtering is Gmail. Local defense is set quite sensibly and rarely makes mistakes.
Anti-spam filters place all suspicious mail in the appropriate category, thereby freeing your inbox from unnecessary advertising junk. Of course, this tool is far from ideal, but still it works noticeably more efficiently than competing analogues.
It is also worth noting the domestic service - "Yandex-Mail". The local filters sort letters very efficiently, sifting the wheat from the chaff. But many advanced users complain about the domestic mailer for the abundance of advertising blocks. Yes, it cleans up the most diverse spam well, but the banner there and the banner here spoil the whole impression, and some even interfere with it normallywork.
In any case, if you have registered an e-mail on some third-party service, then Gmail can be configured to intercept correspondence from any email inbox that supports this function.






