In recent years, online anonymity has taken on a special meaning. Increasingly, signs began to appear in society that freedom on the Internet is just an illusion imposed on ordinary users. In fact, both your ISP and the sites you visit are collecting a lot of information about your behavior. Someone ignores this, and someone is not satisfied that they can follow him. The solution for the latter can be special software known as the Tor browser. Reviews about it, as well as a description of the principles of the program will be given in this article.
What is "Thor"?
Let's start with a definition. The Tor software is a system that allows users to remain anonymous online by redirecting traffic through a network of servers around the world. Due to this, it becomes almost impossible to track which resources the user visits.
The development of this project began in the early 2000s in the United States. Later, the authors of the system managed to raise funding for the implementation of the program. Today, the Tor browser is presented in the form of a program that anyone can download. After thesettings of this software, the user can be hidden from surveillance in many ways. What exactly the program does, read on.

Why do we need Thor?
So, as already noted, the first purpose of this software is to provide anonymity. It is almost impossible to track which resources the user visits, what sites he views. Just as it is impossible to understand the country of origin of this person by encrypting traffic through different servers with which the Tor browser interacts.
Reviews and discussion of the program show another use of this software - the ability to access prohibited resources. In the light of recent political events in the world, this issue is particularly relevant. The restriction set at the provider level regarding the entrance to certain resources is violated due to the inability to establish the fact of a visit. And sites that are blocked for one reason or another, a person can view using the same servers, which are something like a link in this traffic transmission chain.
How to use the Tor browser?
Don't worry that the Tor browser, the reviews of which we are interested in, is something complicated that requires special knowledge, programming skills, and the like. No, in fact, the work in this program is as simple as possible, and as soon as you download it, you will see for yourself. It used to be much more difficult to surf the Internet through the Tor protocol. To date, developers have a readytor browser. By installing it, you can visit your favorite sites just like before.
Many people have never heard of such a software solution. Someone, on the contrary, is only aware of the existence of this product, but does not know how to set up Tor (browser). Actually, it's very easy.
When you run the program for the first time, you will see a window with two alternative options, which you need to choose based on your Internet connection situation. It's very simple: if you think that your ISP is tracking your activities and would like to fight it, you need to make some minimal network settings.
If you are sure that there is no control over you by the network administrator and the provider does not care what sites you view, you should choose the first method - "I would like to connect to the Tor network directly."
As you will see in the following, sites that determine your location will no longer be able to accurately show your city and country of origin. This will be the main indicator of how the Tor browser operates. Reviews indicate that accessing sites banned in your country in this way is as easy as shelling pears.
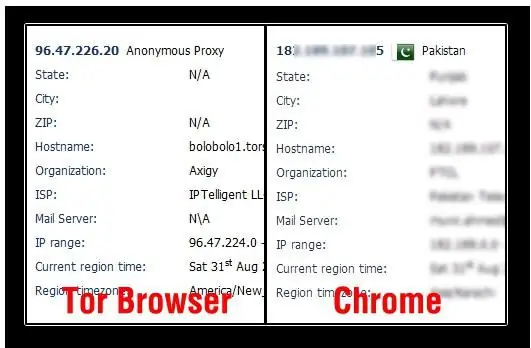
Security threat
There are a lot of rumors on the Internet about what the Tor network really is. Some argue that this is a product of the US military, who wanted to control the world of cybercrime in this way. Others call the Tor network the realm of traffickers in drugs, weapons andvarious terrorists.
However, if you work with this browser to download from your favorite torrent tracker, you are unlikely to become a terrorist, like thousands of other users of this software. Feedback from consumers working with it confirms that this is an easy way to get rid of traffic monitoring or bypass a ban on visiting a resource. So why not use it?
Alternative
Of course, if you do not want to get involved with something new for yourself, it is not necessary to choose the Tor browser as a way to protect personal information.
Reviews indicate that online anonymity can be obtained in other ways, for example, through a VPN connection. It's easier, and for some even more reliable than working with the dubious "Tor" protocol.
In any case, the choice is yours.






